There are several ways to efficiently access the files, folders, and programs in Windows operating system. We can create shortcuts, pin programs to the taskbar, Start menu shortcuts etc. but we can't do it for all programs in many cases. However, the Windows Run Command box is one of the most efficient ways of accessing system programs, folders, and settings.
In this article, I am going to share 15 most important Run commands for Windows users. These commands can make it easier to manage a lot of tasks.
How to open Windows Run command box?
You need to press Win+R (Hold Windows button then Press R)
Important Run Commands Every Windows User Should Know
1. %temp%
This is the fastest way to clear the temporary files from your computer. It can save a lot of space which was being wasted by temporary files.
2. cmd
This command will open the windows DOS command prompt. Windows command prompt is very useful for performing many tasks which are not possible using graphical user interface.
3. MSConfig
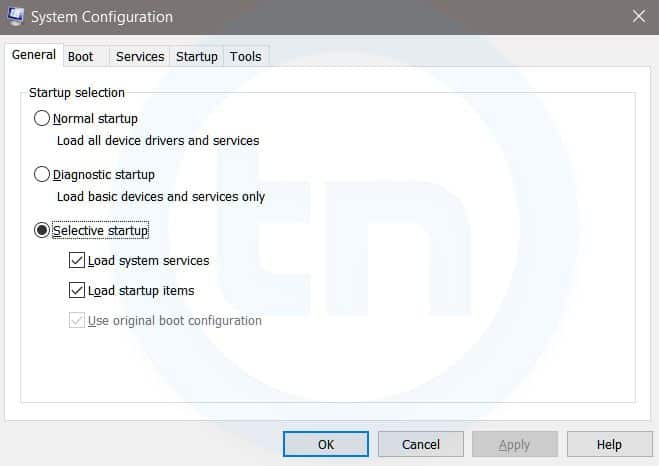
Windows System Configuration
This command will open Windows System Configuration where you can edit different things like the boot options, startup options, services, etc.
4. sysdm.cpl
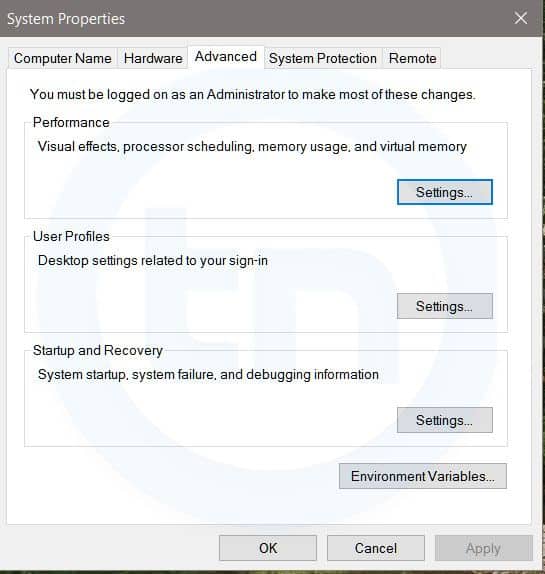
System Properties window
This command will open the System Properties window, Where you can change the system protection and performance related many settings
5. Powershell
Powershell is very similar the command prompt. Just type this command in the Run dialog box, and you will have your PowerShell opened without administrator privileges.
6. perfmon.msc
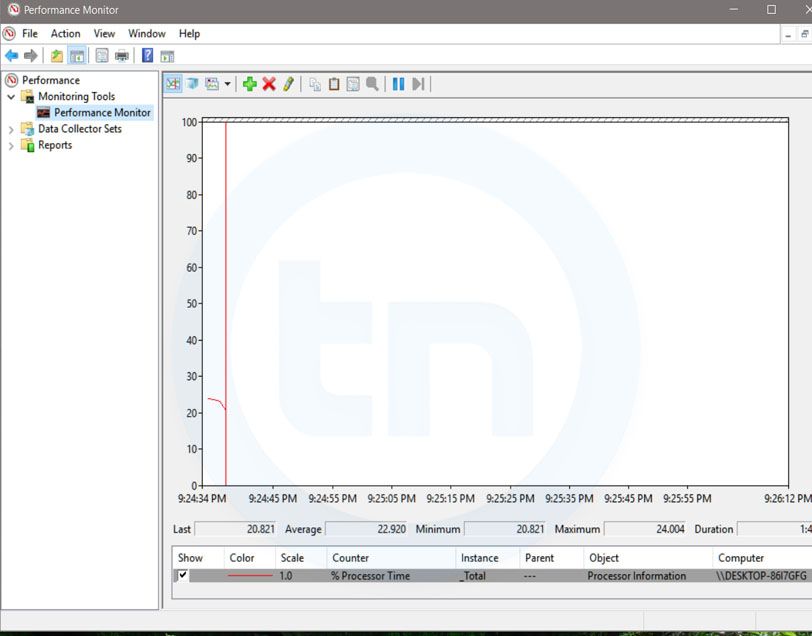
Windows System Performance monitor
This command can be used to monitor the performance of your computer. There are plenty of options for monitoring the system performance
7. regedit
Regedit Run command is used to open the Windows Registry. It is a hierarchical database that hosts all the configurations and settings of Windows operating system, it's users and the installed software.
8. \ (Backslash)
This is one of the lesser known Run commands. Just enter the backslash into the Run dialog box and it will open up the C drive. It is one of the quickest ways to access the C drive.
9. . (Dot)
This is yet another lesser known Run command. When executed, it opens the current user's home folder which hosts all the other local folders like the Downloads, Documents, Desktop, Pictures, etc.
10. .. (Double Dots)
When you execute these two dots in the Run dialog box, it will open up the Users folder which is located directly on the C drive
Also Read; Top 10 Great Gifts For Hackers
11. Control
This command will open the control panel. Control panel is used for managing all the system settings and programs
12. hdwwiz.cpl
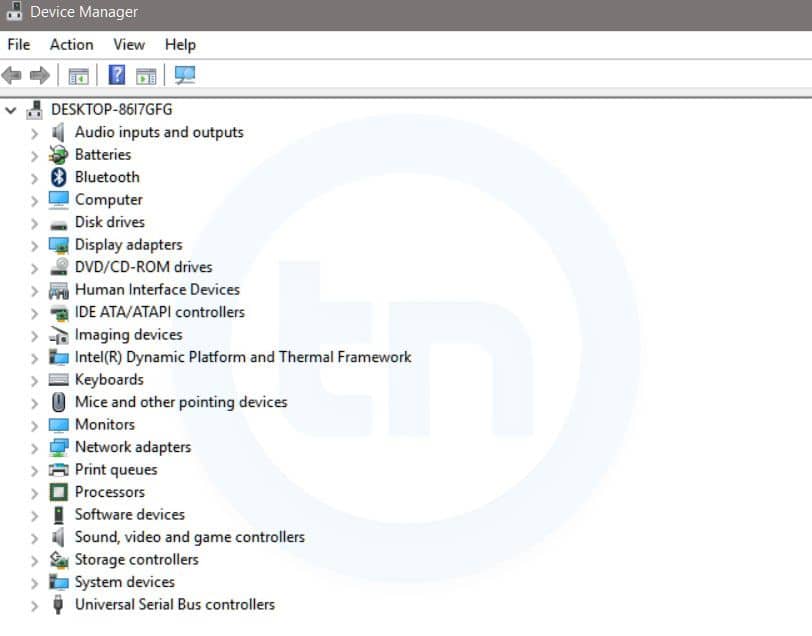
Windows Device Manager
This command is used to open the Device Manager in Windows. You can manage all the device connected internally or externally to your PC.
13. Notepad
The quickest way to open notepad in Windows. Just type this command in Run Box and hit enter.
14. osk
This command will open On-Screen Keyboard on your display monitor. You can easily touch and type or use your mouse for typing.
15. taskmgr
This command will open task manager where you can manage all the processes and programs running on Windows Operating system.
More information
Read more »

























 Digg/username
Digg/username Flickr/username
Flickr/username Myspace/username
Myspace/username Facebook/Your Name
Facebook/Your Name Friendster/Your Name
Friendster/Your Name Virb/username
Virb/username Linkedin/Public Profile Name
Linkedin/Public Profile Name Twitter/username
Twitter/username YouTube/username
YouTube/username Last.fm/username
Last.fm/username Del.icio.us/username
Del.icio.us/username Wikipedia/username
Wikipedia/username Wishlist/Your Name
Wishlist/Your Name GMail/Your Name
GMail/Your Name coComment/username
coComment/username iJigg/username
iJigg/username PureVolume/username
PureVolume/username Upcoming/Your Name
Upcoming/Your Name Kongregate/username
Kongregate/username Zaadz/username
Zaadz/username Technorati/username
Technorati/username MyBlogLog/username
MyBlogLog/username Blog/Your Name
Blog/Your Name



















 Subscribe by email. Enter your email address below:
Subscribe by email. Enter your email address below: 















