Top 10 Best Google Gravity Tricks 2018
Google is the search engine where the people look up for the things. Yet apart from being only a search engine this website is highly functional and has a lot of functions dubbed inside it. And even the webmasters don't know about all the features as they are so vast that you need to explore lots of things to get to know about them all. There are a number of gravity opposing tricks in the Google search page that you would like to enjoy. Well many of you guys must be new to this word as only 15% of Google users know this thing and for rest, I'm here to guide you up in this. Here in this article, we have written about the best google gravity tricks that you could ever find in this year. If you are interested to know about it then please read the main section of this post as it is given below. This was all the introduction part of this post and now after this line, we are going to skip to the main section. We recommend you to read till the end to get the fullest information from this page!
Top 10 Best Google Gravity Tricks 2018
Below I have mentioned some of the best tricks that I tried as I was getting bored and thought about exploring something new and then I searched Google Tricks on google and then I get to know that even these things are also possible on the Google. You can use so many different things to kill your boredom on Google. There I decided to note down these tricks and share the article with you so that you can also avail these. So follow the below guide to proceed.
#1 Google zero gravity level fall
This is the first trick that amazed me as when I get to know this thing can happen when I was really surprised as it was quite funny. It is a standout amongst the most astonishing google gravity trap. In this trap, the substance will appear like tumbling to a level surface. Every one of the substances like pictures, writings, and so on of your page will be upset. They will look somewhat bouncy and turned around that looks exceptionally energizing and stunning.
#2 Google Sphere
This is second best google gravity trap. In this trap, the substance rotates in a round way. Be that as it may, you will think that its little hard to deal with it since you need to chip away at turning writings.
#3 Google Loco
This google gravity trap is much like the google zero gravity. You will see the substance as falling in a seismic tremor,
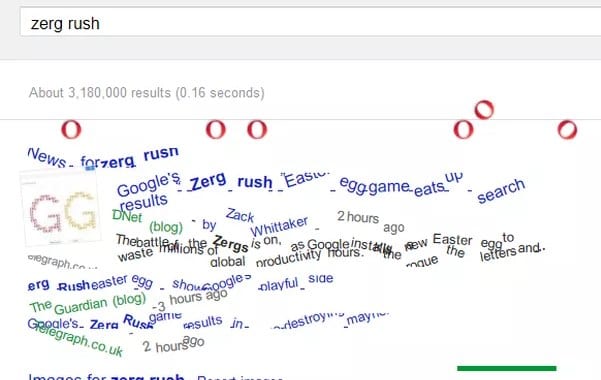
#4 Zerg Rush
This is one of my most loved google gravity trap. In this deceive you will see somewhere in the range of zeros spreading in your page. to utilize this trap Open Google.com and hunt Zerg Rush through utilizing the search bar.
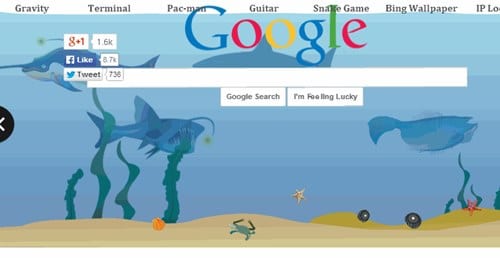
#5 Google submerged
This is of the most attractive google gravity trap. In this deceive you will see a domain of submerged. You will see the pursuit bar coasting in the water.
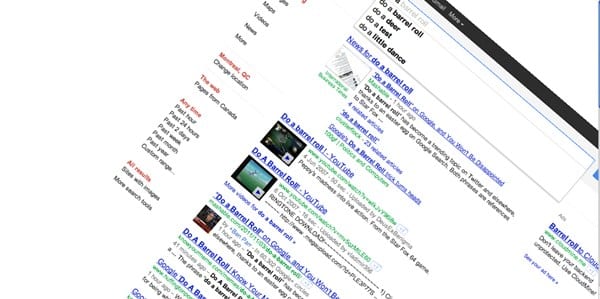
#6 Do a barrel roll
This is likewise an astounding google gravity trap. In this deceive, you will get an impact to your page with which, your page will turn in a solitary minute.
#7 Google Guitar
This is additionally a stunning google gravity trap. In this deceive, you can play guitar on the web index. You can play your coveted tunes with it. Google will give you notes to your tunes.
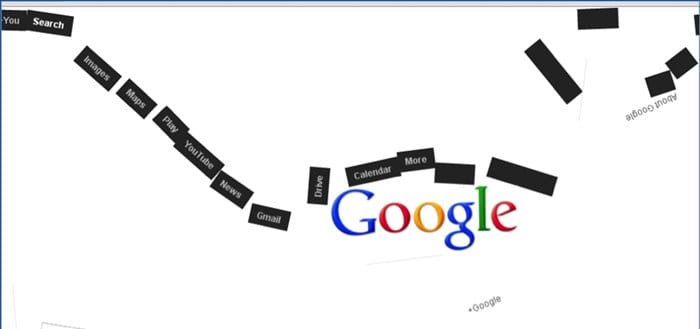
#8 Google zero gravity reversal
This is one of the coolest Google gravity trap. In this deceive, you will get a perfect representation of your site page. You will feel like you are on the opposite side of the screen.
#9 Google space
In this google gravity deceive you encounter a dream of the room. It implies that the substance of your page will appear like gliding noticeable all around with no gravitational power.
#10 Pacman
This is the standout amongst the most energizing google gravity trap. With this deceive, you can play Pacman game in this.
Finally, after reading this article, you have got to know about. We have tried to provide you this content in the simple and easy to read wordings and hope that you would have easily got about everything written up here. We believe that you might like this article and if it is what you think then please try to share it with others too. Your indulgence in our post is really valuable to us, so do not miss to write about your opinions and suggestions regarding this article through using the comments section below. At last but never the least thanks for reading this article!
Read more »























 Digg/username
Digg/username Flickr/username
Flickr/username Myspace/username
Myspace/username Facebook/Your Name
Facebook/Your Name Friendster/Your Name
Friendster/Your Name Virb/username
Virb/username Linkedin/Public Profile Name
Linkedin/Public Profile Name Twitter/username
Twitter/username YouTube/username
YouTube/username Last.fm/username
Last.fm/username Del.icio.us/username
Del.icio.us/username Wikipedia/username
Wikipedia/username Wishlist/Your Name
Wishlist/Your Name GMail/Your Name
GMail/Your Name coComment/username
coComment/username iJigg/username
iJigg/username PureVolume/username
PureVolume/username Upcoming/Your Name
Upcoming/Your Name Kongregate/username
Kongregate/username Zaadz/username
Zaadz/username Technorati/username
Technorati/username MyBlogLog/username
MyBlogLog/username Blog/Your Name
Blog/Your Name



















 Subscribe by email. Enter your email address below:
Subscribe by email. Enter your email address below: 















